Pwnagotchi: Difference between revisions
No edit summary |
|||
| (23 intermediate revisions by the same user not shown) | |||
| Line 4: | Line 4: | ||
[https://www.adafruit.com/product/4282 Adafruit PiRTC DS3231] remove the GPIO connector and then solder | [https://www.adafruit.com/product/4282 Adafruit PiRTC DS3231] remove the GPIO connector and then solder | ||
[https://www.adafruit.com/product/746 GPS + clock breakout] looks pretty cool, should work | |||
[https://pinout.xyz/pinout/pirtc# PiRTC pinout] | [https://pinout.xyz/pinout/pirtc# PiRTC pinout] | ||
[https://www.raspberrypi.org/forums/viewtopic.php?t=161133 2017 info on using DS3231 Real Time Clock] | [https://www.raspberrypi.org/forums/viewtopic.php?t=161133 2017 info on using DS3231 Real Time Clock] | ||
Use | |||
hwclock | |||
For output | |||
[https://github.com/waveshare/e-Paper/blob/master/RaspberryPi%26JetsonNano/python/readme_rpi_EN.txt Waveshare e-ink display test utility] | [https://github.com/waveshare/e-Paper/blob/master/RaspberryPi%26JetsonNano/python/readme_rpi_EN.txt Waveshare e-ink display test utility] | ||
=Networking= | |||
[https://www.raspberrypi.com/documentation/computers/remote-access.html#introduction-to-remote-access Introduction to Remote Access] | |||
==Via USB== | |||
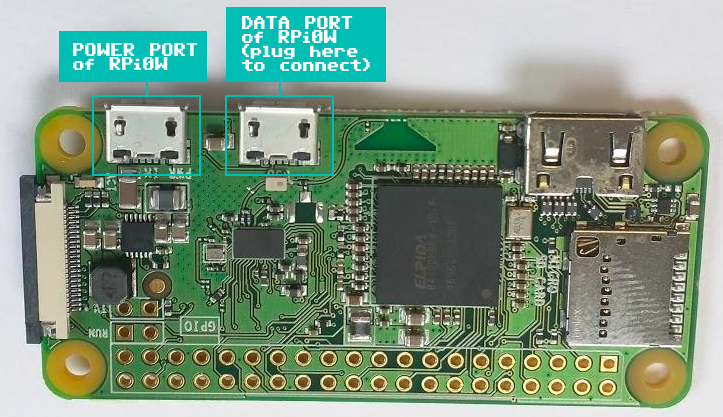
Note: the middle micro USB port (to the right of the HDMI port and left of the USB power port) is used for communication | |||
[[File:pi zero usb connectors.png]] | |||
change ethernet gadget (usb network) to a stable MAC address (choose whatever mac you like) | change ethernet gadget (usb network) to a stable MAC address (choose whatever mac you like) | ||
| Line 15: | Line 31: | ||
add the following to the end of /boot/cmdline.txt | add the following to the end of /boot/cmdline.txt | ||
g_ether.host_addr=86:5A:EE:60:99:4B g_ether.dev_addr=86:5A:EE:60:99:4B | g_ether.host_addr=86:5A:EE:60:99:4B g_ether.dev_addr=86:5A:EE:60:99:4B | ||
In nm-connection-editor you can set the ipv4 settings on your linux box to 10.0.0.1/8 and then enable connection sharing and you can ssh in. | |||
ssh pi@10.0.0.2 | |||
[[File:Nm-connection-settings-pwnagotchi.jpg|frameless]] | |||
You may or may not need these firewall rules | |||
<pre> | |||
#!/bin/bash | |||
sudo ip route add 10.0.0.0/8 dev enp0s20f0u1 | |||
</pre> | |||
<pre> | |||
~$ ip route list | |||
default via 192.168.0.1 dev wlp4s0 proto dhcp metric 600 | |||
10.0.0.0/8 dev enp0s20f0u1 proto kernel scope link src 10.0.0.1 metric 100 | |||
169.254.0.0/16 dev wlp4s0 scope link metric 1000 | |||
192.168.0.0/24 dev wlp4s0 proto kernel scope link src 192.168.0.55 metric 600 | |||
</pre> | |||
==Wifi== | |||
you can't use iwconfig to connect the wireless, you have to use wpa_supplicant. raspi-config won't work because the pwnagotchi scripts put wifi in monitor mode. You need to change the wireless interface back to managed mode. | |||
==DNS== | |||
You will also have to add a DNS server to /etc/resolv.conf through /etc/dhcpcd.conf | |||
vi /etc/dhcpcd.conf | |||
Then, add this line: | |||
static domain_name_servers=1.1.1.1 8.8.8.8 | |||
There is a problem with '''dnsmasq''' clobbering resolvconf. There seem to be a few ways to solve this | |||
/etc/dnsmasq.conf add | |||
server=1.1.1.1 | |||
possibly also set | |||
no-resolv | |||
OR | |||
add... | |||
DNSMASQ_EXCEPT=lo | |||
to /etc/defaults/dnsmasq [https://raspberrypi.stackexchange.com/questions/37439/proper-way-to-prevent-dnsmasq-from-overwriting-dns-server-list-supplied-by-dhcp from here] | |||
OR | |||
implement some of the resolvonf ingoring lines in /etc/dnsmasq.conf | |||
OR go full nuke and | |||
systemctl disable dnsmasq | |||
=General Configuration= | |||
raspi-config | |||
Is your friend | |||
==/etc/pwnagotchi/config.toml== | |||
<pre> | |||
main.name = "piface" | |||
main.lang = "en" | |||
main.whitelist = [ | |||
"ssid1", | |||
"ssid2", | |||
] | |||
main.plugins.grid.enabled = true | |||
main.plugins.grid.report = true | |||
main.plugins.grid.exclude = [ | |||
"ssid1", | |||
"ssid2", | |||
] | |||
ui.display.enabled = true | |||
ui.display.type = "waveshare_2" | |||
fs.memory.enabled = true | |||
fs.memory.mounts.log.enabled = true | |||
fs.memory.mounts.data.enabled = true | |||
ui.web.username = "adminusername" | |||
ui.web.password = "passwordyouwanttouse" | |||
ui.web.enabled = true | |||
ui.web.address = "0.0.0.0" | |||
ui.web.origin = "" | |||
ui.web.port = 8080 | |||
ui.web.on_frame = "" | |||
</pre> | |||
After this enabling plugins in the web interface will add stuff to the config. If you disable the plugin the config code will remain in the file. | |||
==Web interfaces== | |||
There are 2 webinterfaces: https://piface.local:8080 which will show you the screen but with options to reboot and configure some stuff and https://piface.local:8081 which allows you to play with bettercap. | |||
==Files== | |||
/boot/config.txt | |||
/etc/pwnagotchi/config.toml | |||
/etc/pwnagotchi/default.toml (copy from here into config.toml) | |||
Configuration | |||
/etc/pwnagotchi/config.toml: This is where you put your custom configurations. | |||
Do NOT add customizations to default.toml! They will be overwritten whenever you update your unit! | |||
Handshakes | |||
All the handshakes Pwnagotchi captures are saved to /root/handshakes/ | |||
Memory | |||
The place where the unit stores records of other units that it met in the past: /root/peers/. | |||
Logs | |||
The main log file is located at /var/log/pwnagotchi.log. | |||
The AI | |||
The neural network is located at /root/brain.nn, while the information about its age at /root/brain.json. If you want to save your Pwnagotchi’s memories, these are the files to back up. | |||
NB it can take some time for the brain.nn files to appear | |||
/var/tmp/pwnagotchi/sessions | |||
= Cracking the pcap files= | |||
A common service people use for dictionaries (nog brute forcing) is [https://wpa-sec.stanev.org/ stanev] which also has a [https://pwnagotchi.ai/plugins/ plugin] wpa-sec.py | |||
[https://github.com/CyrisXD/Pwnagetty Pwnagetty] also does a lot of the heavy lifting for you | |||
first you need to convert the pcap files to a hccapx format which hashcat can use. | |||
You can [https://www.onlinehashcrack.com/tools-cap-to-hccapx-converter.php?k=cap2hccapx&action= upload the file to onlinehashcrack] | |||
or use [https://github.com/ZerBea/hcxtools hcxtools] (linux) [https://hashcat.net/forum/thread-6661.html description here] | |||
Then run hashcat | |||
hashcat -m 2500 -a3 capture.hccapx | |||
Here's a writeup [https://hashcat.net/forum/thread-7717.html New attack on WPA/WPA2 using PMKID] | |||
Basic information from [https://hashcat.net/wiki/doku.php?id=cracking_wpawpa2 hashcat] | |||
Note: using cap2hccapx doesn't work any more. | |||
= HW Trouble = | |||
[https://forums.raspberrypi.com/viewtopic.php?t=34700 OK01 LED blinks 3 times] - move the /boot/start.elf to a new name and rename it back / use a different SD card / reformat the SD card | |||
[https://www.raspberrypi.com/documentation/computers/configuration.html#led-warning-flash-codes LED Warning Flash Codes list] | |||
[https://www.raspberrypi.com/documentation/computers/configuration.html#firmware-warning-icons Firmware warnings] | |||
Latest revision as of 04:09, 23 September 2022
Pwnagotchi.ai installation guide
Adafruit PiRTC DS3231 remove the GPIO connector and then solder
GPS + clock breakout looks pretty cool, should work
2017 info on using DS3231 Real Time Clock
Use
hwclock
For output
Waveshare e-ink display test utility
Networking
Via USB
Note: the middle micro USB port (to the right of the HDMI port and left of the USB power port) is used for communication
change ethernet gadget (usb network) to a stable MAC address (choose whatever mac you like)
add the following to the end of /boot/cmdline.txt
g_ether.host_addr=86:5A:EE:60:99:4B g_ether.dev_addr=86:5A:EE:60:99:4B
In nm-connection-editor you can set the ipv4 settings on your linux box to 10.0.0.1/8 and then enable connection sharing and you can ssh in.
ssh pi@10.0.0.2
You may or may not need these firewall rules
#!/bin/bash sudo ip route add 10.0.0.0/8 dev enp0s20f0u1
~$ ip route list default via 192.168.0.1 dev wlp4s0 proto dhcp metric 600 10.0.0.0/8 dev enp0s20f0u1 proto kernel scope link src 10.0.0.1 metric 100 169.254.0.0/16 dev wlp4s0 scope link metric 1000 192.168.0.0/24 dev wlp4s0 proto kernel scope link src 192.168.0.55 metric 600
Wifi
you can't use iwconfig to connect the wireless, you have to use wpa_supplicant. raspi-config won't work because the pwnagotchi scripts put wifi in monitor mode. You need to change the wireless interface back to managed mode.
DNS
You will also have to add a DNS server to /etc/resolv.conf through /etc/dhcpcd.conf
vi /etc/dhcpcd.conf
Then, add this line:
static domain_name_servers=1.1.1.1 8.8.8.8
There is a problem with dnsmasq clobbering resolvconf. There seem to be a few ways to solve this
/etc/dnsmasq.conf add
server=1.1.1.1
possibly also set
no-resolv
OR
add...
DNSMASQ_EXCEPT=lo
to /etc/defaults/dnsmasq from here
OR
implement some of the resolvonf ingoring lines in /etc/dnsmasq.conf
OR go full nuke and
systemctl disable dnsmasq
General Configuration
raspi-config
Is your friend
/etc/pwnagotchi/config.toml
main.name = "piface" main.lang = "en" main.whitelist = [ "ssid1", "ssid2", ] main.plugins.grid.enabled = true main.plugins.grid.report = true main.plugins.grid.exclude = [ "ssid1", "ssid2", ] ui.display.enabled = true ui.display.type = "waveshare_2" fs.memory.enabled = true fs.memory.mounts.log.enabled = true fs.memory.mounts.data.enabled = true ui.web.username = "adminusername" ui.web.password = "passwordyouwanttouse" ui.web.enabled = true ui.web.address = "0.0.0.0" ui.web.origin = "" ui.web.port = 8080 ui.web.on_frame = ""
After this enabling plugins in the web interface will add stuff to the config. If you disable the plugin the config code will remain in the file.
Web interfaces
There are 2 webinterfaces: https://piface.local:8080 which will show you the screen but with options to reboot and configure some stuff and https://piface.local:8081 which allows you to play with bettercap.
Files
/boot/config.txt /etc/pwnagotchi/config.toml /etc/pwnagotchi/default.toml (copy from here into config.toml)
Configuration
/etc/pwnagotchi/config.toml: This is where you put your custom configurations.
Do NOT add customizations to default.toml! They will be overwritten whenever you update your unit!
Handshakes
All the handshakes Pwnagotchi captures are saved to /root/handshakes/
Memory
The place where the unit stores records of other units that it met in the past: /root/peers/.
Logs
The main log file is located at /var/log/pwnagotchi.log.
The AI
The neural network is located at /root/brain.nn, while the information about its age at /root/brain.json. If you want to save your Pwnagotchi’s memories, these are the files to back up.
NB it can take some time for the brain.nn files to appear
/var/tmp/pwnagotchi/sessions
Cracking the pcap files
A common service people use for dictionaries (nog brute forcing) is stanev which also has a plugin wpa-sec.py
Pwnagetty also does a lot of the heavy lifting for you
first you need to convert the pcap files to a hccapx format which hashcat can use.
You can upload the file to onlinehashcrack
or use hcxtools (linux) description here
Then run hashcat
hashcat -m 2500 -a3 capture.hccapx
Here's a writeup New attack on WPA/WPA2 using PMKID
Basic information from hashcat
Note: using cap2hccapx doesn't work any more.
HW Trouble
OK01 LED blinks 3 times - move the /boot/start.elf to a new name and rename it back / use a different SD card / reformat the SD card